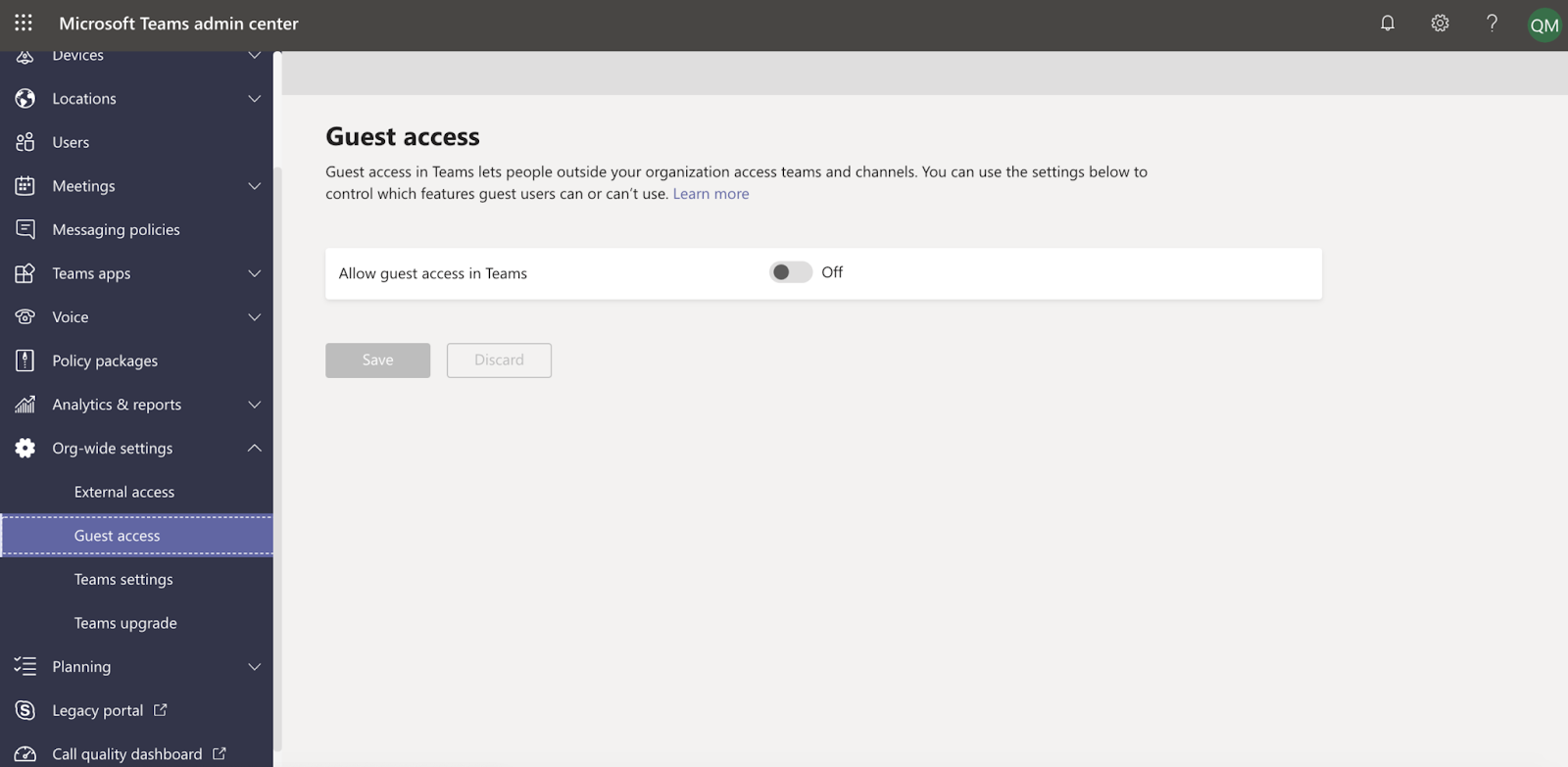
In this article we are going to explain what is Information Barriers for Microsoft Teams as well as comment about its advantages and disadvantages for different businesses types.
Table of contents
1- What is Information Barriers for Microsoft Teams
2- Requirements for Information Barriers
3- Permission Requirements and Prerequisites for Microsoft Teams
4- Capabilities and Limitations
1- What is Information Barriers for Microsoft Teams
Information Barriers for Microsoft was first introduced to the community in May 2019, as a solution to restrict communication and collaboration between groups to avoid any type of conflict of interests or to safeguard information. This kind of solution is not new to the business world (specially, to finance companies) and is known as “Ethical Wall” or “Chinese Walls”.
Corporations, brokerage firms, investment banks, and retail banks have been using Chinese walls to describe situations where there is a need to maintain confidentiality in order to prevent conflicts of interest.
A classic example, addressed by FINRA regulation, is when a financial company (banks, credit rating, etc) that handles non-public information needs to block its investment departments communications with researchers or any other department. Other examples are contact centers that need policies to have agents isolated with each other.
As a more general example, many companies do not let employees communicate with higher ranked positions (although they could choose to allow the opposite) as well as setting different permissions, as file sharing, for specific categories of employees.
2- Requirements for Information Barriers
As this service is not included on Microsoft’s basic packages, companies need to have one of the following subscriptions:
- •Microsoft 365 E5
- •Office 365 E5
- •Office 365 Advanced Compliance
- •Microsoft 365 E5 Information Protection and Compliance
3- Permission Requirements and Prerequisites for Microsoft Teams
As Information Barriers is a product intended for compliance officers (or any other compliance related position) use, in order to define, or edit rules one must be assigned with one of the following roles:
- •Microsoft 365 global administrator
- •Office 365 global administrator
- •Compliance administrator
- •IB Compliance management
There are a few checklist items to have completed in order to get Information Barriers configured
- •Required permission and licenses have been assigned
- •Verify your directory includes data for segmenting users
- •Enable scoped directory search for Microsoft Teams (need to wait 24 hours after enabling)
- •Make sure audit logging is turned on
- •Make sure no Exchange address book are policies are in place
- •Provide admin consent for Microsoft Teams
As this article is not going to deal with the complex process of how to configure Information Barriers, we recommend these by Microsoft expert Tony Redmond:
4- Capabilities and Limitations
Microsoft Information Barriers works blocking files, messages and adding team members using customizable filters such as department, alias, email address. Many custom filters can be set in order to manage the policies. More information here
As for Information Barriers limitations, these are regarding general aspects.
- •Policies can only be set using Powershell. No UI. Can be very difficult for a compliance officer to use.
- •No control of communication with external domain during meetings
- •No control of external Users and guests
- •No auditing of blocked operation that can assist in training
- •No notification for compliance admin
- •No granular control of specific operation – such as screen sharing
- •Policies can be set only to either block files and messages – no control over functionalities such as audio, video and screen sharing
- •If previous address book policies are present they must be deleted before configuring
- •Policies can take several hours to apply after configuration
As for users that want to know how to overcome these limitations and gain extra functionality to the Information Barriers, we recommend checking SphereShield Ethical Wall for Microsoft Teams.
SphereShield by AGAT provides a powerful yet intuitive solution to control communications in Microsoft Teams offering advanced options such as audio, video/screen sharing and granular control.
Here is a short Demo
For a more comprehensive understanding, check this comparison table
| Ethical Wall | |||
| Office 365 | AGAT | ||
| License → | Essential/E3 | E5 – Information Barriers | SPT2 (E.W. License) |
| Internal control by Groups/Users (Allow/Block) | ❌ | ✅ | ✅ |
| External Control By External User (Allow/Block) | ❌ | ❌ | ✅ |
| External Control by Internal group/users/domain | ❌ | ❌ | ✅ |
| Granular Control capabilities (IM’s/files/audio/video/sharing) | ❌ | ❌ | ✅ |
| Can be fully controlled by compliance role only | ❌ | ❌ | ✅ |
| Web User Interface (GUI) – Easy to operate | N/A | ❌ | ✅ |
| Notifications to end user/admin | ❌ | ❌ | ✅ |
| Incident auditing for compliance awareness and training | ❌ | ❌ | ✅ |
| Reports by user/policy/domain | ❌ | ❌ | ✅ |
| External system integration/SIEM | ❌ | ❌ | ✅ |
| Restrict Guests communication only to Team members | ❌ | ❌ | ✅ |
| Restrict access for guest only to specific channels in a team | ❌ | ❌ | ✅ |
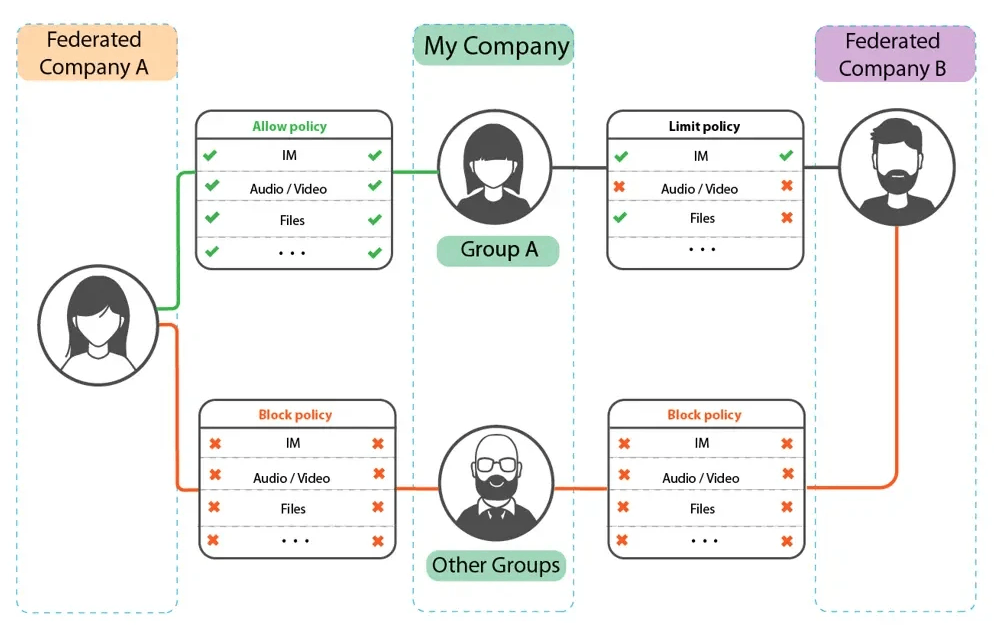
Contact Us for more information