In this 3 part series, we will be going over 10 security threats to Microsoft Teams.
Introduction: The Growth of Microsoft Teams
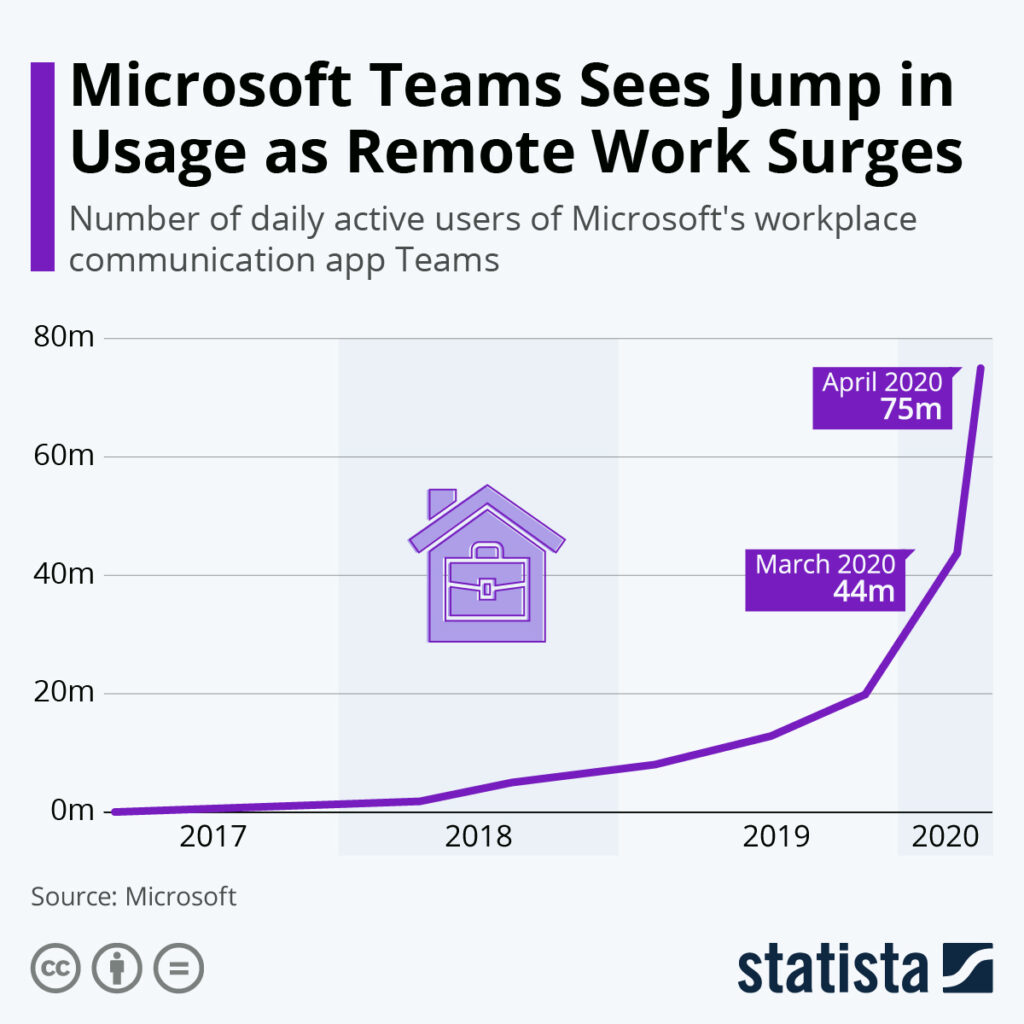
Microsoft has recently released statistics about Teams users, and they have revealed remarkable growth. It has grown to 75 million users from about 20 million over a 12-month span (from late winter of 2019 to early spring 2020). Users include guest participants – in fact, there was an average of 200 million participants meeting in just one day in the month of April. 66% of Microsoft Teams users share files through the app. The amount of companies that have integrated independent apps with Microsoft Teams has also tripled.
Because growth has continued unabated, risk and security groups must recognize Microsoft Teams as the go-to collaboration tool, as well as a data conduit that goes outside of and within organizations. They must make sure that the security of Microsoft Teams is prioritized. More often than not, it is quicker and easier for users to collaborate through the use of Microsoft Teams with existing defense systems in play. Policies applicable to the sharing of files by way of email, cloud storage, and USB sticks must be enforced.
Users won’t accept Microsoft Teams’ features being switched off altogether or hobbled in any way. The following series will address the biggest security threats practitioners should plan for. It will provide ideas to optimize the value that Microsoft Teams offers while keeping data secure.
One big concern involves the amount of guests that can be added to Microsoft Teams. Also of concern are the amount of independent apps that can be incorporated into Microsoft Teams’ channels, since both could contribute to data loss.
There are just over 2900 guests, on average, that are added every month to Microsoft Teams by administrators and owners. As such, IT security staff must have the ability to control and monitor their access. For context, completely open access can be likened to opening up corporate meeting rooms, but without any visitors signing into a guestbook. 29,000 visitors equates to a new visitor joining every time 10 minutes has passed, all day long. It isn’t very hard to add guests to Microsoft Teams, then share information with them that is sensitive. Users may forget that visitors are part of the group. Therefore, security will require a couple of controls – managing immediate guest additions, and being able to review prior visitor access.
Microsoft Teams usage can serve as a conduit of sorts to systems not part of the Microsoft ecosystem – ones that could serve as a potential data loss outlet. A user’s ability to integrate third-party apps can be described as a “Shadow IT” variation. It includes the very same security threats that other “Shadow IT” forms come with.
Security groups must be able to review third-party apps through the use of several security attributes for the sake of blocking them – including ones that don’t conform to specific corporate standards.
First Threat: Guest Users
Once a guest is added, they’ll be able to see sensitive/internal content.
Microsoft Teams allows you to add outside users (a.k.a. guests) to channels so that files and chat messages can be shared. After access is given, guests will be able to have meetings online, create shifts and tasks for users, make phone calls, have live meetings, and use integrated apps with both external and internal collaborators. Several companies have been using Microsoft Teams to engage with customers – especially ones with customer service responsibilities. Any administrator or chat or owner has the ability to add members to channels. Based on settings, that may include outside guests. Multiple administrators can be part of a team channel, which is quite common whenever channels have a lot of members (particularly across different time zones). Whenever guests get added, they’ll either have the ability to see prior chat histories (which include files), or be limited to viewing recent content.
Microsoft allows administrators to disable or enable “guest access” as part of Teams’ security capabilities. By default, this feature is not automatically enabled for guests.
The problem with implementation of a complete enterprise setting revolves around the fact that some groups will be closed to guests, while others are completely open to them. Further, tenant administrators that want different settings must make the applicable changes for their respective team. Many organizations are interested in using all of the capabilities that come with Microsoft Teams. As such, they generally allow guests to have the same access administrators do.
Flexibility is truly needed here. Being able to establish internal exclusive teams – ones that are limited to authorized external parties and public teams – is key. By modifying blocklist or allowed list domains, better security will be implemented, giving employees the flexibility they need to collaborate with various authorized guests on Microsoft Teams.
You can do the following in order to optimize security:
- Remove and detect guest users if unauthorized domains try to join team channels.
- Remove and detect guest users that join groups only intended for internal discussions.
- Regulate messages that are posted on channels, as well as chat discussions involving guest users originating from specific domains.
- Regulate files posted on chat discussions and channels that involve guest users originating from specific domains.
- Regulate files and messages historically posted in channels that have guest users originating from specific domains.
- Report guest users and channels so that team members can be managed accordingly.
- Several actions must be available based on the policy trigger’s severity, whether that entails quarantining, tombstoning, or removing files; sending alerts to IT administrators and channel owners; and making sure that logs get chronicled for upcoming investigations, if necessary.
Having the ability to remove or monitor sensitive messages and content, as well as granting permission to trust the domains, lets guests access Microsoft Teams without compromising the security of data.
You can create new groups whenever you want. Members might not be sure what attributes they have, so some kind of security policy should be established beforehand.
For better control of Guests in Microsoft Teams, we recommend using SphereShield Ethical Wall for Microsoft Teams. It lets the company decide which specific permissions Guests have (messages, calls, video, files) and allows to set granular rules regarding communication.
Second Threat: Access from Untrusted Locations or Unmanaged Devices
Microsoft Teams may be accessed by devices that are unmanaged, which could lead to a loss of data.
Standard Microsoft Teams access involves the usual name/password duo, and multifactor authentication is an option. Valid users will be able to log in on just about any type of device. Users who have access from unmanaged devices are able to download files that are shared on a Microsoft Teams channel. Those files will either be lost or forwarded if said users are cyberattack victims.
Being able to establish policies for specific unmanaged devices allows you to protect Microsoft Teams’ content. You’ll also be able to do the following:
- Lock unmanaged device access.
- Block downloads but allow access.
- Block files from being uploaded (just in case unmanaged devices are malware-infected) but allow access.
- Add specific DLP (data loss prevention) policies for various unmanaged devices.
- Step up redirection authentication (a redirect to a different authentication mechanism).
- Block any unmanaged device from accessing the native Microsoft Teams client.
- Proxy an unmanaged device with access that is browser-based (for extra controls).
- Force DRM (digital rights management) registration prior to access.
Accessibility from certain devices in locations that aren’t trusted could result in data loss.
One big risk indicator is data location. Based on how sensitive the data is, IT administrators should consider defining locations as either trusted or on trusted. They should either disallow or allow access, or establish security policies depending on the location.
Block and allow IP location/address lists might contain corporate offices or entire countries. Certain policies would prove to be quite useful, including the following:
- Blocking access from certain blocklists.
- Permitting access from either IP geography or range, but still block downloads.
- Set up redirection authentication (a redirect to a different authentication mechanism).
- Proxy certain devices from either IP geography or range with access that is browser-based (for extra controls).
- Add certain DLP policies for devices based on IP geography/range.
- Blocking devices from either IP geography or range so they cannot access the native Microsoft Teams client.
- Make DRM registration mandatory before access.
For better access control AGAT Software offers 2 solutions
SphereShield Conditional Access for Microsoft Teams provides companies using Microsoft Teams the option to prohibit users from accessing organizational Microsoft Teams from unmanaged and non-compliant devices.
SphereShield integrates seamlessly with leading UEM services MobileIron, McAfee, Symantec, BlackBerry, AirWatch, Forcepoint, Citrix, Maas360 and Microsoft Itune.
SphereShield Risk Engine for Microsoft Teams monitors all successful or failed connections to an O365 tenant and displays a live map of connections. Define Geo location rules to control access to your data.
Third Threat: Screen Sharing and Confidential Information
Confidential information can be inadvertently leaked through screen sharing.
The screen sharing feature on Microsoft Teams is quite powerful and convenient for meetings. Users have the option to share individual application files on a full screen. They can also jointly share their whiteboards. This feature is accessible to guests and internal users.
However, if a user were to overshare sensitive data, problems will ensue. Emails, new groups, and incoming messages might be shown on a presenter’s screen, which is then shown to various attendees. If a full screen is shared, there might be another application that reveals confidential data. Even if they are running in the background, communication apps are capable of revealing things they shouldn’t.
IT administrators are encouraged to think about configuring the Microsoft Teams app. The screen sharing feature should be disabled so that only application sharing is allowed. That way, alerts will not be shown on other member’s screens during a meeting. There are several options for guests and users when it comes to sharing implementation. However, this takes away a feature that users enjoy – one that is widely used. If a certain speaker wanted to display numerous applications, then they’ll need to do so through each individual app while the meeting is taking place.
You can either allow or disable screen sharing for guest users. When doing so, though, you need to determine if this will actually be a potential risk for you. How would the company be affected if a staff member sees confidential information disclosed by an outside party?
Users also have the ability to share their whiteboards. Data loss isn’t as likely with this feature, and administrators will need to determine a suitable organization policy.
Instead of an administrator attempting to guess possible eventualities, it would be more prudent to emphasize employee training, as far as Microsoft Teams usage is concerned. Explanations and examples should be included that go over the pros and cons of these feature sets. That way, users can choose when messaging apps should be closed, when individual files should be shared, and when a full screen is okay to share.
Sphereshield Compliance Recording And Analysis For Microsoft Teams performs Audio and Video analysis on recorded meetings for DLP and eDiscovery needs. It Analyses on-screen video with OCR being able to detect DLP Incidents and showing them on eDiscovery
SphereShield Ethical Wall for Microsoft Teams can block screen sharing using granular rules. Based on Internal/External users and more options.
Stay tuned for our next delivery.